设计模式之观察者模式
本文共 6026 字,大约阅读时间需要 20 分钟。
模式定义:
定义了对象之间的一对多依赖,让多个观察者对象同时监听某一个主题
对象,当主题对象发生变化时,它的所有依赖者都会收到通知并更新
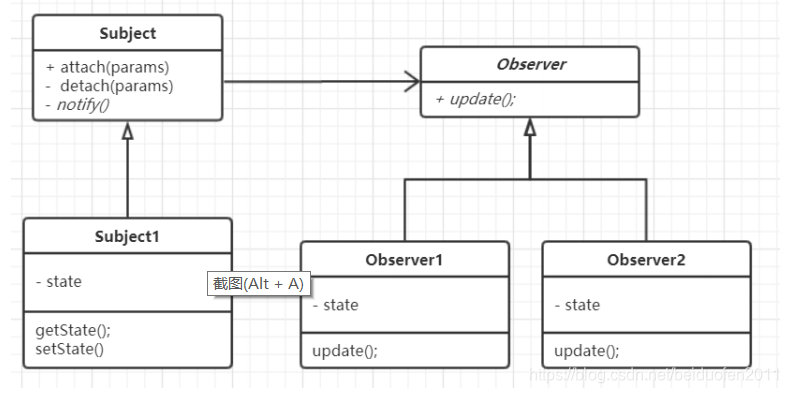
应用场景:
当更改一个对象的状态可能需要更改其他对象,并且实际的对象集事先
未知或动态更改时,请使用观察者模式。
优点:
1.符合开闭原则
2. 可以在运行时建立对象之间的关系
JDK&Spring源码中的应用
1 JDK :
2 java . util . Observable
3 Spring :
4 org . springframework . context . ApplicationListener
public interface Subject { public void registerObserver(Observer o); public void removeObserver(Observer o); public void notifyObservers();} package com.fen.dou.sjms.observer;import java.util.ArrayList;/** *类是核心 *1. 包含最新的天气情况信息 *2. 含有 观察者集合,使用 ArrayList 管理 *3. 当数据有更新时,就主动的调用 ArrayList, 通知所有的(接入方)就看到最新的信息 *@author Administrator * */public class WeatherData implements Subject { private float temperatrue; private float pressure; private float humidity; //观察者集合 private ArrayList observers;//加入新的第三方 public WeatherData() { observers =new ArrayList (); } public float getTemperature() { return temperatrue; } public float getPressure() { return pressure; } public float getHumidity() { return humidity; } public void dataChange() { //调用 接入方的 update notifyObservers(); } //当数据有更新时,就调用 setData public void setData(float temperature, float pressure, float humidity) { this.temperatrue = temperature; this.pressure = pressure; this.humidity = humidity; //调用 dataChange, 将最新的信息 推送给 接入方 currentConditions dataChange(); } //注册一个观察者 @Override public void registerObserver(Observer o) { // TODO Auto-generated method stub observers.add(o); } //移除一个观察者 @Override public void removeObserver(Observer o) {// TODO Auto-generated method stub if(observers.contains(o)) { observers.remove(o); } //遍历所有的观察者,并通知 @Override public void notifyObservers() {// TODO Auto-generated method stub for(int i = 0; i < observers.size(); i++) { observers.get(i).update(this.temperatrue, this.pressure, this.humidity); } }} package com.fen.dou.sjms.observer;//观察者接口,有观察者来实现public interface Observer { public void update(float temperature, float pressure, float humidity);} package com.fen.dou.sjms.observer;public class BaiduSite implements Observer { // 温度,气压,湿度 private float temperature; private float pressure; private float humidity; // 更新 天气情况,是由 WeatherData 来调用,我使用推送模式 public void update(float temperature, float pressure, float humidity) { this.temperature = temperature; this.pressure = pressure; this.humidity = humidity; display(); } // 显 示 public void display() { System.out.println("===百度网站===="); System.out.println("***百度网站 气温 : " + temperature + "***"); System.out.println("***百度网站 气压: " + pressure + "***"); System.out.println("***百度网站 湿度: " + humidity + "***"); }} package com.fen.dou.sjms.observer;public class CurrentConditions implements Observer { // 温度,气压,湿度 private float temperature; private float pressure; private float humidity; // 更新 天气情况,是由 WeatherData 来调用,我使用推送模式 public void update(float temperature, float pressure, float humidity) { this.temperature = temperature; this.pressure = pressure; this.humidity = humidity; display(); } // 显 示 public void display() { System.out.println("***Today mTemperature: " + temperature + "***"); System.out.println("***Today mPressure: " + pressure + "***"); System.out.println("***Today mHumidity: " + humidity + "***"); }} package com.fen.dou.sjms.observer;public class Client { public static void main(String[] args) { // TODO Auto-generated method stub //创建一个 WeatherData WeatherData weatherData = new WeatherData(); //创建观察者 CurrentConditions currentConditions = new CurrentConditions(); BaiduSite baiduSite = new BaiduSite(); // 注 册 到 weatherData weatherData.registerObserver(currentConditions); weatherData.registerObserver(baiduSite); // 测 试 System.out.println("通知各个注册的观察者, 看看信息"); weatherData.setData(10f, 100f, 30.3f); weatherData.removeObserver(currentConditions); //测试System.out.println(); System.out.println("通知各个注册的观察者, 看看信息"); weatherData.setData(10f, 100f, 30.3f); }} org.springframework.context.ApplicationListener中的使用
public class MyEvent extends ApplicationContextEvent { public MyEvent(ApplicationContext source) { super(source); } public void out(String name) { System.out.println("MyEvent 事件执行了 name :"+name); }}
import org.springframework.context.ApplicationListener;public class MyListenerA implements ApplicationListener{ @Override public void onApplicationEvent(MyEvent event) { System.out.println("MyListenerA 执行了"); event.out("wangmingyuan not love"); }}
import org.springframework.context.ApplicationListener;public class MyListenerB implements ApplicationListener{ @Override public void onApplicationEvent(MyEvent event) { System.out.println("MyListenerB 执行了"); event.out("wangmingyuan not love"); }}
public class MyPublisher implements ApplicationContextAware { public ApplicationContext applicationContext; @Override public void setApplicationContext(ApplicationContext applicationContext) throws BeansException { this.applicationContext=applicationContext; } public void publisherEvent(ApplicationEvent event) { System.out.println("-----发送事件-----"+event); applicationContext.publishEvent(event); }}
@Import(value = {MyEvent.class,MyListenerA.class,MyListenerB.class,MyPublisher.class})public class EventTest { public static void main(String[] args) { AnnotationConfigApplicationContext context=new AnnotationConfigApplicationContext(EventTest.class); MyPublisher myPublisher = context.getBean(MyPublisher.class); MyEvent myEvent = context.getBean(MyEvent.class); myPublisher.publisherEvent(myEvent); }} 
转载地址:http://bwwrz.baihongyu.com/
你可能感兴趣的文章
mysql 常见问题
查看>>
MYSQL 幻读(Phantom Problem)不可重复读
查看>>
mysql 往字段后面加字符串
查看>>
mysql 快速自增假数据, 新增假数据,mysql自增假数据
查看>>
Mysql 批量修改四种方式效率对比(一)
查看>>
Mysql 报错 Field 'id' doesn't have a default value
查看>>
MySQL 报错:Duplicate entry 'xxx' for key 'UNIQ_XXXX'
查看>>
Mysql 拼接多个字段作为查询条件查询方法
查看>>
mysql 排序id_mysql如何按特定id排序
查看>>
Mysql 提示:Communication link failure
查看>>
mysql 插入是否成功_PDO mysql:如何知道插入是否成功
查看>>
Mysql 数据库InnoDB存储引擎中主要组件的刷新清理条件:脏页、RedoLog重做日志、Insert Buffer或ChangeBuffer、Undo Log
查看>>
mysql 数据库中 count(*),count(1),count(列名)区别和效率问题
查看>>
mysql 数据库备份及ibdata1的瘦身
查看>>
MySQL 数据库备份种类以及常用备份工具汇总
查看>>
mysql 数据库存储引擎怎么选择?快来看看性能测试吧
查看>>
MySQL 数据库操作指南:学习如何使用 Python 进行增删改查操作
查看>>
MySQL 数据库的高可用性分析
查看>>
MySQL 数据库设计总结
查看>>
Mysql 数据库重置ID排序
查看>>